Whether companies want to preserve data sovereignty or achieve compliance with regulatory requirements, there are many reasons for trusted and reliable cloud encryption: ultimately, they need to be sure that their valuable data and those of their customers are optimally protected against unauthorized access. There are several ways to achieve this. This post looks at a cloud data protection solution, the eperi Gateway, to explain how cloud data can be effectively protected, and what needs to be kept in mind when choosing a suitable data protection solution.
 What to look for when choosing an integrated cloud data protection platform
What to look for when choosing an integrated cloud data protection platform
The most effective approach for protecting sensitive data in the cloud is encryption and pseudonymization. There are several solutions and approaches here: from Cloud Access Security Broker (CASB) to Bring Your Own Key (BYOK), all work reliably and protect the customer’s data to the best of their abilities.
CASB services or applications are located between the user and the cloud platform and work to control, monitor, and log data flows in their entirety. In the BYOK model, the cloud provider encrypts the data by using cryptographic keys that are provided by the cloud customers themselves.
When evaluating these approaches, three important aspects need to be considered: data control, usability, and data protection. The concept of data control says something about who controls the keys that are necessary for encryption – and therefore also has access to the encrypted data. Usability considers the extent to which the cloud applications and their functionality remain usable with no restrictions despite the encryption of their data. Finally, data protection involves asking ourselves whether trade-offs have to be made in terms of data security and protection in order to maintain the usability of the cloud application or individual functions within the application.
And, as the data controller responsible for data protection, one also has to decide which of these three aspects is the most important – since it is still unfortunately true that the approaches and solutions on the market do not accommodate all of these aspects equally well.
While CASB services essentially offer a high level of data protection and full data control, usability is typically sub-optimal since a lot of work will be necessary to customize the service to the various cloud applications and specialized functionality. In the worst case, there is nothing else to do but block a cloud service completely, if it can not be integrated securely.
In stark contrast, BYOK approaches from the various cloud providers cleverly promote usability and data protection as selling points – but these come at the expense of data control. This is because, despite the cryptographic keys required being provided by the user, the cloud provider also has full access to the same keys. And this can potentially impact data control concerns since this control is no longer held exclusively by the company as the cloud user.
And so we have now arrived at the point where you are probably asking: isn’t there a cloud encryption solution that actually scores well across the board in all three disciplines? And, as you may have guessed: yes there is, namely eperi Cloud Data Protection (CDP). With this solution, you can be confident of being able to avoid compromises for any of the three aspects.
This is because no cloud providers or processors gain access to your keys (= optimum data control), the cloud application remains virtually unaffected by the encryption (= high usability), and there are no trade-offs for data protection, either, since the eperi Gateway on which the eperi Cloud Data Protection Platform is built uses an engine co-developed by the German Federal Office for Information Security (BSI) that works with standard encryption methods and algorithms, and its code can be publicly audited since it is freely available as open source software.
What the eperi Gateway can do
As a cloud data encryption solution, the eperi Gateway handles a wide variety of tasks:
– Encryption and pseudonymization of data before they are transferred to the cloud application
– Full handling of cryptographic key management
– And ensuring the consistent application of data protection policies across all devices and platforms.
For the eperi Gateway, it makes no difference whether integration involves internal or external cloud applications, databases, or data storage systems. All integration uses a well-designed template model, which we will be returning to shortly.
The eperi Gateway provides this comprehensive level of data protection in two ways: first, by using end-to-end encryption and pseudonymization of data before these are transferred to the target or cloud application, and second, by using internal key management. Accordingly, only customers themselves have access to the private keys. In terms of data control, this offers a substantial advantage over other solutions.
Thanks to its transparent proxy architecture, the eperi Gateway can also be integrated into any IT environment without major customization work being required. This offers a very simple approach to handling and avoids the need to make modifications to underlying systems or existing workflows. Paired with the template model, the encryption techniques and methods also ensure the flexible deployment of encryption, especially in the context of sensitive data that are stored and processed in the cloud applications.
How the eperi Gateway works
Essentially, the eperi Gateway can best be understood in its role as a ‘broker’. As such, it is located outside the cloud environment whose data are to be encrypted, and therefore decouples the cloud applications from the cloud data. It is also functions as a reverse, forward, and API proxy, depending on the application and access scenario. At the same time, the eperi Gateway acts as the ‘guardian’ of all of the keys required for pseudonymizing and encrypting the plaintext data. This offers both external and internal users transparent access to the cloud data that is secure at all times. In this context, ‘transparent’ should be understood to mean that the background encryption produces no noticeable effects for users, and that no installations are required on the user or target systems.
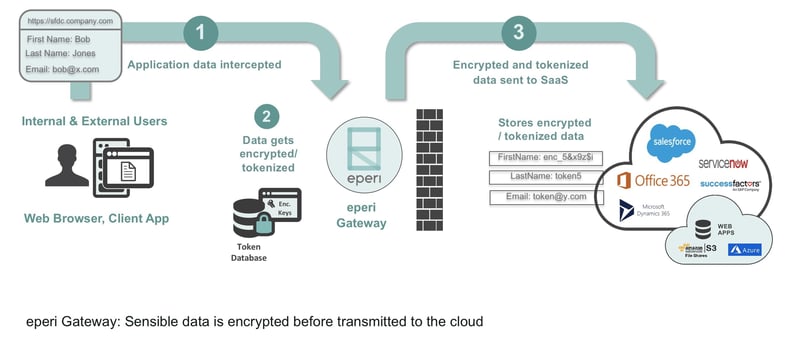
How the eperi Gateway works as a proxy
In general terms, a proxy server is a broker device that handles network communications between two end points, while also being responsible for a wide variety of separate tasks. In the case of the eperi Gateway, for example, these tasks include the encryption and decryption of the data passed between these end points.
Essentially, the eperi Gateway functions as a forward and reverse proxy. In these cases, users first access the eperi Gateway from their network and pass their data to the Gateway, which then encrypts these data before forwarding them on to the corresponding cloud application. All of this takes place in the background without involving the user.
In the opposite direction, the eperi Gateway functions as a proxy server that accepts the stream of data that is returned by a cloud application and then decrypts the encrypted data inside it before forwarding these data on to the clients in plaintext.
When the eperi Gateway is working as a reverse proxy, customers can provide vanity URLs for access to the application. Instead of https://www.cloud-application.com, for example, users can access http://cloud-application.company.com. In the forward proxy configuration, the eperi Gateway is entered into the web browser or application settings as a proxy server and accessed in the background as soon as the user wishes to access the target system. Of course, the eperi Gateway can also be integrated into an existing proxy chain, if proxy servers are already in use at the company.
Last but not least, the eperi Gateway can also be integrated into existing application architectures by means of various API interfaces. As an example, this would be required if the encryption and decryption is deployed merely as an upstream or downstream process, or if support needs to be offered for proprietary protocols.
Excursion: An explanation of the eperi Gateway template model
As a result of the template model it uses, the eperi Gateway can be deployed for virtually any cloud and application environment – including databases, applications, and file systems. Predesigned templates exist for Microsoft Office 365, Salesforce, Oracle and MS SQL databases, for example, and can be used either out-of-the-box or with only minor adjustments being required.
The templates specify the kind of encryption to be used for fields in the target application. The encryption method to be used can therefore be selected for each field defined. As an example, a target application may require values to confirm to certain formats for a specific field, in order to accept an email address, for example, or a value may need to be within a certain range – in order to process dates of birth or zip codes, for example. Since the use of standard encryption techniques on these fields would cause errors, a tokenization approach to encryption must be selected for such fields, which clearly specifies the schema for generating replacement values that conform to the required type.
Another appealing feature of the template approach is the fact that it uses special XML files that can also contain executable Java code – offering a way to expand the eperi Gateway with custom functionality. This also applies for workflow definitions. The templates define these using BPEL (Business Process Execution Language) to specify exactly how and where the data are stored and processed.
Alongside the existing templates that are already customized to suit the respective applications, eperi’s customers and partners can also create their own templates. This is done using the Application Analyzer, which ensures that the eperi Gateway automatically identifies the data to be encrypted within the data stream and processes it using prescribed pseudonymization methods.
Summary
Choosing the right cloud data protection platform is becoming an increasingly important decision. This is why it is certainly an excellent idea to know the nuts and bolts of the underlying techniques that they use. At the end of the day, knowing how data are encrypted and at which point in the process is the only way for companies to be sure of selecting the right solution. And it is exactly for this reason that the eperi Gateway is always the right choice: since it offers an optimal balance of the aspects of data control, usability, and data protection. While also having a number of interesting approaches and advantages up its sleeve.




