No IT security technology can preclude the possibility of a successful attack on corporate systems and applications. However, if the worst-case scenario does occur then encrypting sensitive data prevents the exploitation of stolen or illegally published information. A safeguard like this is indispensable when relocating applications to the Cloud.
BY ELMAR EPERIESI-BECK, EPERI
 Relocating business processes and information to the Cloud has become a common tactic to save on resources and guarantee productivity. However, this method also means that those IT and business managers responsible for data protection are walking a tightrope, without a safety net. Companies can be lulled into a false sense of security when they hand over IT security, data and applications to Cloud providers, relying only on Service Level Agreements. The responsibility for data security lies squarely with the company itself.
Relocating business processes and information to the Cloud has become a common tactic to save on resources and guarantee productivity. However, this method also means that those IT and business managers responsible for data protection are walking a tightrope, without a safety net. Companies can be lulled into a false sense of security when they hand over IT security, data and applications to Cloud providers, relying only on Service Level Agreements. The responsibility for data security lies squarely with the company itself.
And the requirements are becoming ever more stringent: Since coming into force in May 2018, the European General Data Protection Regulation (EU GDPR) has laid down binding conditions for data protection and defined requirements for data security - including the Cloud. When relocating data, organizations need a last line of defense to prevent illegal exploitation of data if unauthorized access takes place.
Correct Encryption - Everywhere, Now
Not every form of encryption is secure enough. The highest possible level of security is only guaranteed, if data is encrypted at every point of storage and processing - “In Use”, “In Transit” and “At Rest”. Every location and every application that makes data available as plain text represents a potential security breach. End-to-end encryption is extremely important for data that is stored and processed in the Cloud.
When implemented correctly, standardized and tested encryption procedures such as AES 256 and RSA 2048 provide optimum security. If the necessary precautions are not taken, it is easy to find a way around solutions that change standard encryption to allow search and sort operations to be performed in encrypted data.
No Productivity Restrictions
Data security does not have to negatively impact corporate processes and procedures. Gateway-based procedures support authorized users as they work with the data - without placing restrictions on important functions, such as performing data searches.
Functionality emulators within data encryption, only available to authorized users via a gateway application, allow work to continue on databases as if there were no encryption in place.
Tokenization procedures also allow authorized users to work with data that only they see as plain text. For all other data, substitute values are displayed. To tokenize information, a gateway generates values appropriate to type for each data record. This guarantees that application workflows continue to function and that only the substitute value is stored in the Cloud. However, secure tokenization is important for data security. Older procedures often use mapping tables to store these substitute values appropriate to type, making them a popular target for hackers. Therefore, it is important to encrypt the original data before making entries in the token table, thus combining encryption and tokenization.
Swift Realization of Data Security
Encryption solutions must provide security without changing the existing IT infrastructure and restricting the functionality of applications. Increased flexibility is an important factor in the decision to migrate data to the Cloud. Fast implementation saves money. This is particularly important for safeguarding data centers. Positioned in front of the actual IT infrastructure, a gateway structure that performs encryption and functional emulation outside of the application to be protected ensures that existing IT infrastructure is not restricted and allows swift implementation of encryptions.
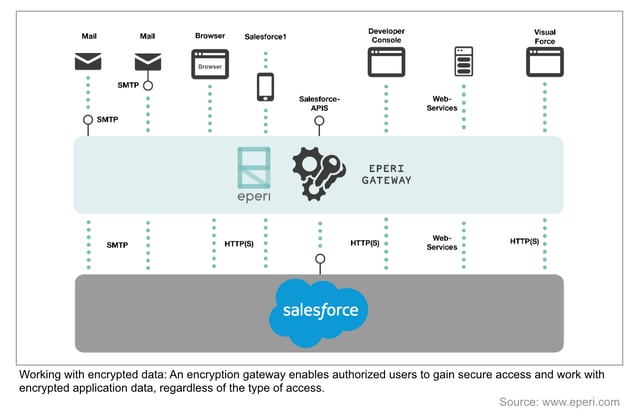
Clearly Defined Responsibilities - Especially When Moving to the Cloud
Data security, especially in the Cloud, requires consistency in the regulation and assignment of access rights to keys and data. Secure solutions mean that there is no question about who is responsible for the generation and administration of cryptographic keys - your company. Neither the providers of the encryption solution or the application, nor the operators and administrators of Cloud data centers, have access to the keys. The administrator in the data center can use encrypted data to perform all necessary tasks such as copying, moving, triggering backups, mirroring or migration. This division of responsibilities renders futile any external, third-party requests for information about the keys, or for decryption.
The group of key administrators within your company should also be kept as small as possible. The best solution is for a few selected security administrators to manage the cryptographic keys. They can then assign and withdraw these without ever having to access plain text data. The authorized user then relies on the IT administrator to manage access rights, using a meta directory for example. Rights are assigned in the application that encrypts the data, such as Salesforce or Outlook 365.
Compliance
An encryption solution helps companies to meet ever-stricter data protection requirements. The tightening of data protection laws and the introduction of new regulations, such as the NIS Directive or EU GDPR, mean that this topic is becoming even more critical.
Correct encryption implementation documents pseudonymization or encryption of personal data (according to Article 32 of EU GDPR) and helps to meet requirements for selection of suitable protection technology (EU GDPR Article 25), for administrative access management with user rights (EU GDPR Article 32), for minimizing data processing (EU GDPR Article 5) when the only data to leave the company is encrypted and useless for third parties, or for centralizing data protection (EU GDPR Article 36). This basis for compliance provides secure data encryption and is particularly important in the Cloud, as it is not possible to assess and secure the IT infrastructure there to the same degree as is possible with an on-premise architecture.
Regulate Competences
The division of powers is also especially important when relocating data to the Cloud. Models for data trusteeship, with the obligation for providers of applications and Cloud-based data centers to commit to the division of powers, represent the beginnings of a transparent allocation of expertise for the benefit of data security. A strict functional division is important here: The solution provider guarantees application functionality, while the Cloud provider supplies storage space and adheres to the Service Level Agreement. To guarantee maximum security, access to keys and the methods to generate these keys, which in turn allow plain text data to be read, must remain the responsibility of the customer. This is a key competency that must not be surrendered in any division of powers.
The only guarantee of real data security is a gateway solution that couples a range of cryptographic procedures with the appropriate user authorizations and infrastructure, ensuring that companies retain control of their data and keys. This creates the final line of defense mentioned above, just in case someone really does try to gain unauthorized access to data.




